Microsoft.AspNetCore.RateLimiting 中间件提供速率限制中间件。 应用可配置速率限制策略,然后将策略附加到终结点。 使用速率限制的应用在部署前应仔细测试并查看其负载。 有关详细信息,请参阅本文中的 测试具有速率限制的终结点 。
速率限制器算法 类 RateLimiterOptionsExtensions 提供以下用于速率限制的扩展方法:
固定窗口限制器 方法 AddFixedWindowLimiter 使用固定的时间范围来限制请求。 当时间范围过期时,将启动一个新的时间窗口,并重置请求限制。
考虑下列代码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 using Microsoft.AspNetCore.RateLimiting;using System.Threading.RateLimiting;var builder = WebApplication.CreateBuilder(args);builder.Services.AddRateLimiter(_ => _ .AddFixedWindowLimiter(policyName: "fixed" , options => { options.PermitLimit = 4 ; options.Window = TimeSpan.FromSeconds(12 ); options.QueueProcessingOrder = QueueProcessingOrder.OldestFirst; options.QueueLimit = 2 ; })); var app = builder.Build();app.UseRateLimiter(); static string GetTicks ()0x11111 ).ToString("00000" );app.MapGet("/" , () => Results.Ok($"Hello {GetTicks()} " )) .RequireRateLimiting("fixed" ); app.Run();
前面的代码:
应用应使用 配置 来设置限制器选项。 以下代码使用 MyRateLimitOptions 更新上述代码进行配置:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 using System.Threading.RateLimiting;using Microsoft.AspNetCore.RateLimiting;using WebRateLimitAuth.Models;var builder = WebApplication.CreateBuilder(args);builder.Services.Configure<MyRateLimitOptions>( builder.Configuration.GetSection(MyRateLimitOptions.MyRateLimit)); var myOptions = new MyRateLimitOptions();builder.Configuration.GetSection(MyRateLimitOptions.MyRateLimit).Bind(myOptions); var fixedPolicy = "fixed" ;builder.Services.AddRateLimiter(_ => _ .AddFixedWindowLimiter(policyName: fixedPolicy, options => { options.PermitLimit = myOptions.PermitLimit; options.Window = TimeSpan.FromSeconds(myOptions.Window); options.QueueProcessingOrder = QueueProcessingOrder.OldestFirst; options.QueueLimit = myOptions.QueueLimit; })); var app = builder.Build();app.UseRateLimiter(); static string GetTicks ()0x11111 ).ToString("00000" );app.MapGet("/" , () => Results.Ok($"Fixed Window Limiter {GetTicks()} " )) .RequireRateLimiting(fixedPolicy); app.Run();
滑动窗口限制器 滑动窗口算法:
类似于固定窗口限制器,但为每个窗口添加段。 窗口每个段间隔滑动一个段。 段间隔是 (窗口时间) / (每个窗口) 段。
将窗口的请求限制为 permitLimit 请求。
每个时间窗口按段划分 n 。
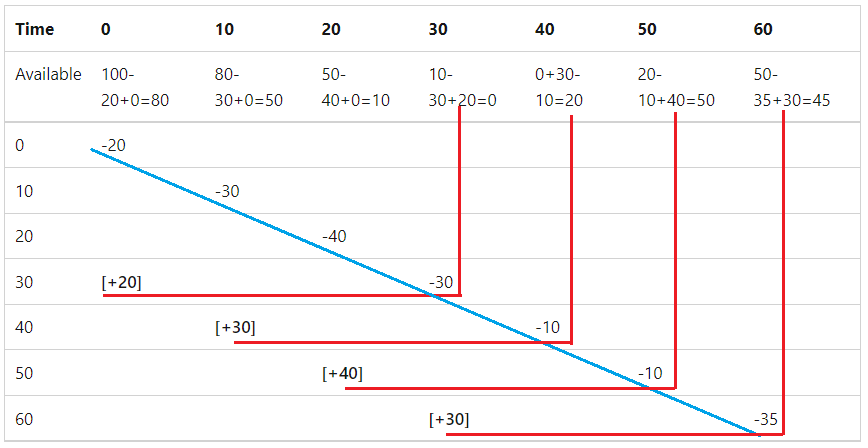
从当前时间段) n 之前的已过期时间段 (段返回的请求将添加到当前时间段。 我们将一个窗口后过期时间段称为过期时间段。 请考虑下表,其中显示了一个滑动窗口限制器,该限制器具有 30 秒的窗口、每个窗口 3 个段和 100 个请求的限制:
首行和第一列显示时间段。
第二行显示剩余的可用请求。 其余请求是可用请求+回收的。
每次请求都沿对角线蓝线移动。
从 30 日开始,从过期时间段获取的请求将添加回请求限制,如红线所示。
下表以不同的格式显示了上图中的数据。 “ 剩余” 列显示上一段 (上一行) 的 “结存 ”中可用的请求。 第一行显示 100 个可用,因为没有以前的段:
时间
可用
采取
已从过期时间回收
结日
0
100
20
0
80
10
80
30
0
50
20
50
40
0
10
30
10
30
20
0
40
0
10
30
20
50
20
10
40
50
60
50
35
30
45
以下代码使用滑动窗口速率限制器:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 using Microsoft.AspNetCore.RateLimiting;using System.Threading.RateLimiting;using WebRateLimitAuth.Models;var builder = WebApplication.CreateBuilder(args);var myOptions = new MyRateLimitOptions();builder.Configuration.GetSection(MyRateLimitOptions.MyRateLimit).Bind(myOptions); var slidingPolicy = "sliding" ;builder.Services.AddRateLimiter(_ => _ .AddSlidingWindowLimiter(policyName: slidingPolicy, options => { options.PermitLimit = myOptions.PermitLimit; options.Window = TimeSpan.FromSeconds(myOptions.Window); options.SegmentsPerWindow = myOptions.SegmentsPerWindow; options.QueueProcessingOrder = QueueProcessingOrder.OldestFirst; options.QueueLimit = myOptions.QueueLimit; })); var app = builder.Build();app.UseRateLimiter(); static string GetTicks ()0x11111 ).ToString("00000" );app.MapGet("/" , () => Results.Ok($"Sliding Window Limiter {GetTicks()} " )) .RequireRateLimiting(slidingPolicy); app.Run();
令牌桶限制程序 令牌桶限制器类似于滑动窗口限制程序,但每次补货期间都会添加固定数量的令牌,而不是添加从过期段获取的请求。 添加的每个段的令牌不能将可用令牌增加到高于令牌桶限制的数字。 下表显示了令牌存储桶限制器,其限制为 100 个令牌,补货期为 10 秒:
时间
可用
采取
已添加
结日
0
100
20
0
80
10
80
10
20
90
20
90
5
15
100
30
100
30
20
90
40
90
6
16
100
50
100
40
20
80
60
80
50
20
50
以下代码使用令牌存储桶限制程序:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 using Microsoft.AspNetCore.RateLimiting;using System.Threading.RateLimiting;using WebRateLimitAuth.Models;var builder = WebApplication.CreateBuilder(args);var tokenPolicy = "token" ;var myOptions = new MyRateLimitOptions();builder.Configuration.GetSection(MyRateLimitOptions.MyRateLimit).Bind(myOptions); builder.Services.AddRateLimiter(_ => _ .AddTokenBucketLimiter(policyName: tokenPolicy, options => { options.TokenLimit = myOptions.TokenLimit; options.QueueProcessingOrder = QueueProcessingOrder.OldestFirst; options.QueueLimit = myOptions.QueueLimit; options.ReplenishmentPeriod = TimeSpan.FromSeconds(myOptions.ReplenishmentPeriod); options.TokensPerPeriod = myOptions.TokensPerPeriod; options.AutoReplenishment = myOptions.AutoReplenishment; })); var app = builder.Build();app.UseRateLimiter(); static string GetTicks ()0x11111 ).ToString("00000" );app.MapGet("/" , () => Results.Ok($"Token Limiter {GetTicks()} " )) .RequireRateLimiting(tokenPolicy); app.Run();
当 设置为 时AutoReplenishment ,内部计时器每隔一次ReplenishmentPeriod 补充令牌;如果设置为 false,应用必须在限制器上调用 TryReplenish 。true
并发限制器 并发限制程序限制并发请求数。 每个请求都会将并发限制减少 1。 请求完成后,限制将增加 1。 与限制指定时间段内请求总数的其他请求限制器不同,并发限制程序仅限制并发请求数,不限制一段时间内的请求数。
以下代码使用并发限制器:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 using Microsoft.AspNetCore.RateLimiting;using System.Threading.RateLimiting;using WebRateLimitAuth.Models;var builder = WebApplication.CreateBuilder(args);var concurrencyPolicy = "Concurrency" ;var myOptions = new MyRateLimitOptions();builder.Configuration.GetSection(MyRateLimitOptions.MyRateLimit).Bind(myOptions); builder.Services.AddRateLimiter(_ => _ .AddConcurrencyLimiter(policyName: concurrencyPolicy, options => { options.PermitLimit = myOptions.PermitLimit; options.QueueProcessingOrder = QueueProcessingOrder.OldestFirst; options.QueueLimit = myOptions.QueueLimit; })); var app = builder.Build();app.UseRateLimiter(); static string GetTicks ()0x11111 ).ToString("00000" );app.MapGet("/" , async () => { await Task.Delay(500 ); return Results.Ok($"Concurrency Limiter {GetTicks()} " ); }).RequireRateLimiting(concurrencyPolicy); app.Run();
创建链接的限制器 API CreateChained 允许传入合并为一个 PartitionedRateLimiter的多个 PartitionedRateLimiter 。 组合的限制器按顺序运行输入限制器。
以下代码使用 CreateChained:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 using System.Globalization;using System.Threading.RateLimiting;var builder = WebApplication.CreateBuilder(args);builder.Services.AddRateLimiter(_ => { _.OnRejected = (context, _) => { if (context.Lease.TryGetMetadata(MetadataName.RetryAfter, out var retryAfter)) { context.HttpContext.Response.Headers.RetryAfter = ((int ) retryAfter.TotalSeconds).ToString(NumberFormatInfo.InvariantInfo); } context.HttpContext.Response.StatusCode = StatusCodes.Status429TooManyRequests; context.HttpContext.Response.WriteAsync("Too many requests. Please try again later." ); return new ValueTask(); }; _.GlobalLimiter = PartitionedRateLimiter.CreateChained( PartitionedRateLimiter.Create<HttpContext, string >(httpContext => { var userAgent = httpContext.Request.Headers.UserAgent.ToString(); return RateLimitPartition.GetFixedWindowLimiter (userAgent, _ => new FixedWindowRateLimiterOptions { AutoReplenishment = true , PermitLimit = 4 , Window = TimeSpan.FromSeconds(2 ) }); }), PartitionedRateLimiter.Create<HttpContext, string >(httpContext => { var userAgent = httpContext.Request.Headers.UserAgent.ToString(); return RateLimitPartition.GetFixedWindowLimiter (userAgent, _ => new FixedWindowRateLimiterOptions { AutoReplenishment = true , PermitLimit = 20 , Window = TimeSpan.FromSeconds(30 ) }); })); }); var app = builder.Build();app.UseRateLimiter(); static string GetTicks ()0x11111 ).ToString("00000" );app.MapGet("/" , () => Results.Ok($"Hello {GetTicks()} " )); app.Run();
有关详细信息,请参阅 CreateChained 源代码
EnableRateLimiting 和 DisableRateLimiting 属性[EnableRateLimiting] 和 [DisableRateLimiting] 属性可以应用于控制器、操作方法或 Razor Page。
属性[DisableRateLimiting]禁用 RequireRateLimiting 以对所有控制器终结点应用 fixedPolicy 速率限制:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 using Microsoft.AspNetCore.RateLimiting;using System.Threading.RateLimiting;using WebRateLimitAuth.Models;var builder = WebApplication.CreateBuilder(args);builder.Services.AddRazorPages(); builder.Services.AddControllersWithViews(); builder.Services.Configure<MyRateLimitOptions>( builder.Configuration.GetSection(MyRateLimitOptions.MyRateLimit)); var myOptions = new MyRateLimitOptions();builder.Configuration.GetSection(MyRateLimitOptions.MyRateLimit).Bind(myOptions); var fixedPolicy = "fixed" ;builder.Services.AddRateLimiter(_ => _ .AddFixedWindowLimiter(policyName: fixedPolicy, options => { options.PermitLimit = myOptions.PermitLimit; options.Window = TimeSpan.FromSeconds(myOptions.Window); options.QueueProcessingOrder = QueueProcessingOrder.OldestFirst; options.QueueLimit = myOptions.QueueLimit; })); var slidingPolicy = "sliding" ;builder.Services.AddRateLimiter(_ => _ .AddSlidingWindowLimiter(policyName: slidingPolicy, options => { options.PermitLimit = myOptions.SlidingPermitLimit; options.Window = TimeSpan.FromSeconds(myOptions.Window); options.SegmentsPerWindow = myOptions.SegmentsPerWindow; options.QueueProcessingOrder = QueueProcessingOrder.OldestFirst; options.QueueLimit = myOptions.QueueLimit; })); var app = builder.Build();app.UseRateLimiter(); if (!app.Environment.IsDevelopment()){ app.UseExceptionHandler("/Error" ); app.UseHsts(); } app.UseHttpsRedirection(); app.UseStaticFiles(); app.MapRazorPages().RequireRateLimiting(slidingPolicy); app.MapDefaultControllerRoute().RequireRateLimiting(fixedPolicy); app.Run();
在以下代码中, [DisableRateLimiting] 禁用速率限制和替代应用于 Home2Controller 中的 Program.cs和 app.MapDefaultControllerRoute().RequireRateLimiting(fixedPolicy) 调用的 [EnableRateLimiting("fixed")] 重写:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 [EnableRateLimiting("fixed" ) ] public class Home2Controller : Controller { private readonly ILogger<Home2Controller> _logger; public Home2Controller (ILogger<Home2Controller> logger ) { _logger = logger; } public ActionResult Index () { return View(); } [EnableRateLimiting("sliding" ) ] public ActionResult Privacy () { return View(); } [DisableRateLimiting ] public ActionResult NoLimit () { return View(); } [ResponseCache(Duration = 0, Location = ResponseCacheLocation.None, NoStore = true) ] public IActionResult Error () { return View(new ErrorViewModel { RequestId = Activity.Current?.Id ?? HttpContext.TraceIdentifier }); } }
在前面的代码中, [EnableRateLimiting("sliding")]未 Privacy 因为 Program.cs 调用 app.MapDefaultControllerRoute().RequireRateLimiting(fixedPolicy)了 。
请考虑以下不调用 RequireRateLimitingMapRazorPages 或 MapDefaultControllerRoute的代码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 using Microsoft.AspNetCore.RateLimiting;using System.Threading.RateLimiting;using WebRateLimitAuth.Models;var builder = WebApplication.CreateBuilder(args);builder.Services.AddRazorPages(); builder.Services.AddControllersWithViews(); builder.Services.Configure<MyRateLimitOptions>( builder.Configuration.GetSection(MyRateLimitOptions.MyRateLimit)); var myOptions = new MyRateLimitOptions();builder.Configuration.GetSection(MyRateLimitOptions.MyRateLimit).Bind(myOptions); var fixedPolicy = "fixed" ;builder.Services.AddRateLimiter(_ => _ .AddFixedWindowLimiter(policyName: fixedPolicy, options => { options.PermitLimit = myOptions.PermitLimit; options.Window = TimeSpan.FromSeconds(myOptions.Window); options.QueueProcessingOrder = QueueProcessingOrder.OldestFirst; options.QueueLimit = myOptions.QueueLimit; })); var slidingPolicy = "sliding" ;builder.Services.AddRateLimiter(_ => _ .AddSlidingWindowLimiter(policyName: slidingPolicy, options => { options.PermitLimit = myOptions.SlidingPermitLimit; options.Window = TimeSpan.FromSeconds(myOptions.Window); options.SegmentsPerWindow = myOptions.SegmentsPerWindow; options.QueueProcessingOrder = QueueProcessingOrder.OldestFirst; options.QueueLimit = myOptions.QueueLimit; })); var app = builder.Build();app.UseRateLimiter(); if (!app.Environment.IsDevelopment()){ app.UseExceptionHandler("/Error" ); app.UseHsts(); } app.UseHttpsRedirection(); app.UseStaticFiles(); app.MapRazorPages(); app.MapDefaultControllerRoute(); app.MapRazorPages(); app.MapDefaultControllerRoute(); app.Run();
考虑以下控制器:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 [EnableRateLimiting("fixed" ) ] public class Home2Controller : Controller { private readonly ILogger<Home2Controller> _logger; public Home2Controller (ILogger<Home2Controller> logger ) { _logger = logger; } public ActionResult Index () { return View(); } [EnableRateLimiting("sliding" ) ] public ActionResult Privacy () { return View(); } [DisableRateLimiting ] public ActionResult NoLimit () { return View(); } [ResponseCache(Duration = 0, Location = ResponseCacheLocation.None, NoStore = true) ] public IActionResult Error () { return View(new ErrorViewModel { RequestId = Activity.Current?.Id ?? HttpContext.TraceIdentifier }); } }
在前面的控制器中:
策略 "fixed" 速率限制器应用于没有 EnableRateLimiting 和 DisableRateLimiting 属性的所有操作方法。
策略 "sliding" 速率限制器应用于操作 Privacy 。
操作方法上 NoLimit 禁用了速率限制。
相同的规则适用于 Razor Pages。 属性 DisableRateLimiting 禁用 Page 上的 Razor 速率限制。 EnableRateLimiting仅应用于Razor未 MapRazorPages().RequireRateLimiting(Policy) Page。
限制器算法比较 固定、滑动和令牌限制器都限制一段时间内的最大请求数。 并发限制程序仅限制并发请求数,不限制一段时间内的请求数。 选择限制程序时,应考虑终结点的成本。 终结点的成本包括使用的资源,例如时间、数据访问、CPU 和 I/O。
速率限制器示例 以下示例不适用于生产代码,而是有关如何使用限制器的示例。
具有 OnRejected、 RetryAfter和 的限制器 GlobalLimiter 以下示例:
创建当请求超过指定限制时调用的 RateLimiterOptions.OnRejected 回调。 retryAfter可以与 、 FixedWindowLimiter ,因为这些算法能够估计何时将添加更多许可证。 ConcurrencyLimiter无法计算何时提供许可证。
添加以下限制器:
实现 SampleRateLimiterPolicy 接口的 IRateLimiterPolicy<TPartitionKey> 。 SampleRateLimiterPolicy类将在本文后面部分介绍。
SlidingWindowLimiter:
为每个经过身份验证的用户使用分区。
所有匿名用户的一个共享分区。
GlobalLimiter 应用于所有请求的 。 将首先执行全局限制器,然后执行特定于终结点的限制器(如果存在)。 GlobalLimiter为每个 IPAddress 创建一个分区。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 using System.Globalization;using System.Net;using System.Threading.RateLimiting;using Microsoft.AspNetCore.Identity;using Microsoft.EntityFrameworkCore;using WebRateLimitAuth;using WebRateLimitAuth.Data;using WebRateLimitAuth.Models;var builder = WebApplication.CreateBuilder(args);var connectionString = builder.Configuration.GetConnectionString("DefaultConnection" ) ?? throw new InvalidOperationException("Connection string 'DefaultConnection' not found." ); builder.Services.AddDbContext<ApplicationDbContext>(options => options.UseSqlServer(connectionString)); builder.Services.AddDatabaseDeveloperPageExceptionFilter(); builder.Services.AddDefaultIdentity<IdentityUser>(options => options.SignIn.RequireConfirmedAccount = true ) .AddEntityFrameworkStores<ApplicationDbContext>(); builder.Services.Configure<MyRateLimitOptions>( builder.Configuration.GetSection(MyRateLimitOptions.MyRateLimit)); builder.Services.AddRazorPages(); builder.Services.AddControllersWithViews(); var userPolicyName = "user" ;var helloPolicy = "hello" ;var myOptions = new MyRateLimitOptions();builder.Configuration.GetSection(MyRateLimitOptions.MyRateLimit).Bind(myOptions); builder.Services.AddRateLimiter(limiterOptions => { limiterOptions.OnRejected = (context, cancellationToken) => { if (context.Lease.TryGetMetadata(MetadataName.RetryAfter, out var retryAfter)) { context.HttpContext.Response.Headers.RetryAfter = ((int ) retryAfter.TotalSeconds).ToString(NumberFormatInfo.InvariantInfo); } context.HttpContext.Response.StatusCode = StatusCodes.Status429TooManyRequests; context.HttpContext.RequestServices.GetService<ILoggerFactory>()? .CreateLogger("Microsoft.AspNetCore.RateLimitingMiddleware" ) .LogWarning("OnRejected: {GetUserEndPoint}" , GetUserEndPoint(context.HttpContext)); return new ValueTask(); }; limiterOptions.AddPolicy<string , SampleRateLimiterPolicy>(helloPolicy); limiterOptions.AddPolicy(userPolicyName, context => { var username = "anonymous user" ; if (context.User.Identity?.IsAuthenticated is true ) { username = context.User.ToString()!; } return RateLimitPartition.GetSlidingWindowLimiter(username, _ => new SlidingWindowRateLimiterOptions { PermitLimit = myOptions.PermitLimit, QueueProcessingOrder = QueueProcessingOrder.OldestFirst, QueueLimit = myOptions.QueueLimit, Window = TimeSpan.FromSeconds(myOptions.Window), SegmentsPerWindow = myOptions.SegmentsPerWindow }); }); limiterOptions.GlobalLimiter = PartitionedRateLimiter.Create<HttpContext, IPAddress>(context => { IPAddress? remoteIpAddress = context.Connection.RemoteIpAddress; if (!IPAddress.IsLoopback(remoteIpAddress!)) { return RateLimitPartition.GetTokenBucketLimiter (remoteIpAddress!, _ => new TokenBucketRateLimiterOptions { TokenLimit = myOptions.TokenLimit2, QueueProcessingOrder = QueueProcessingOrder.OldestFirst, QueueLimit = myOptions.QueueLimit, ReplenishmentPeriod = TimeSpan.FromSeconds(myOptions.ReplenishmentPeriod), TokensPerPeriod = myOptions.TokensPerPeriod, AutoReplenishment = myOptions.AutoReplenishment }); } return RateLimitPartition.GetNoLimiter(IPAddress.Loopback); }); }); var app = builder.Build();if (app.Environment.IsDevelopment()){ app.UseMigrationsEndPoint(); } else { app.UseExceptionHandler("/Error" ); app.UseHsts(); } app.UseHttpsRedirection(); app.UseStaticFiles(); app.UseRouting(); app.UseRateLimiter(); app.UseAuthentication(); app.UseAuthorization(); app.MapRazorPages().RequireRateLimiting(userPolicyName); app.MapDefaultControllerRoute(); static string GetUserEndPoint (HttpContext context ) $"User {context.User.Identity?.Name ?? "Anonymous" } endpoint:{context.Request.Path} " + $" {context.Connection.RemoteIpAddress} " ; static string GetTicks ()0x11111 ).ToString("00000" );app.MapGet("/a" , (HttpContext context) => $"{GetUserEndPoint(context)} {GetTicks()} " ) .RequireRateLimiting(userPolicyName); app.MapGet("/b" , (HttpContext context) => $"{GetUserEndPoint(context)} {GetTicks()} " ) .RequireRateLimiting(helloPolicy); app.MapGet("/c" , (HttpContext context) => $"{GetUserEndPoint(context)} {GetTicks()} " ); app.Run();
警告
在客户端 IP 地址上创建分区会使应用容易受到采用 IP 源地址欺骗的拒绝服务攻击。 有关详细信息,请参阅 BCP 38 RFC 2827 网络入口筛选:击败采用 IP 源地址欺骗的拒绝服务攻击 。
有关完整Program.cs文件,请参阅示例存储库 。
SampleRateLimiterPolicy 类
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 using System.Threading.RateLimiting;using Microsoft.AspNetCore.RateLimiting;using Microsoft.Extensions.Options;using WebRateLimitAuth.Models;namespace WebRateLimitAuth ;public class SampleRateLimiterPolicy : IRateLimiterPolicy <string >{ private Func<OnRejectedContext, CancellationToken, ValueTask>? _onRejected; private readonly MyRateLimitOptions _options; public SampleRateLimiterPolicy (ILogger<SampleRateLimiterPolicy> logger, IOptions<MyRateLimitOptions> options ) { _onRejected = (ctx, token) => { ctx.HttpContext.Response.StatusCode = StatusCodes.Status429TooManyRequests; logger.LogWarning($"Request rejected by {nameof (SampleRateLimiterPolicy)} " ); return ValueTask.CompletedTask; }; _options = options.Value; } public Func<OnRejectedContext, CancellationToken, ValueTask>? OnRejected => _onRejected; public RateLimitPartition<string > GetPartition (HttpContext httpContext ) { return RateLimitPartition.GetSlidingWindowLimiter(string .Empty, _ => new SlidingWindowRateLimiterOptions { PermitLimit = _options.PermitLimit, QueueProcessingOrder = QueueProcessingOrder.OldestFirst, QueueLimit = _options.QueueLimit, Window = TimeSpan.FromSeconds(_options.Window), SegmentsPerWindow = _options.SegmentsPerWindow }); } }
在前面的代码中, OnRejected 使用 OnRejectedContext 将响应状态设置为 429 请求过多 。 默认拒绝状态为 503 服务不可用 。
具有授权的限制器 以下示例使用 JSON Web 令牌 (JWT) ,并使用 JWT 访问令牌 创建分区。 在生产应用中,JWT 通常由充当安全令牌服务 (STS) 的服务器提供。 对于本地开发,dotnet user-jwts 命令行工具可用于创建和管理特定于应用的本地 JWT。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 using System.Threading.RateLimiting;using Microsoft.AspNetCore.Authentication;using Microsoft.Extensions.Primitives;using WebRateLimitAuth.Models;var builder = WebApplication.CreateBuilder(args);builder.Services.AddAuthorization(); builder.Services.AddAuthentication("Bearer" ).AddJwtBearer(); var myOptions = new MyRateLimitOptions();builder.Configuration.GetSection(MyRateLimitOptions.MyRateLimit).Bind(myOptions); var jwtPolicyName = "jwt" ;builder.Services.AddRateLimiter(limiterOptions => { limiterOptions.RejectionStatusCode = StatusCodes.Status429TooManyRequests; limiterOptions.AddPolicy(policyName: jwtPolicyName, partitioner: httpContext => { var accessToken = httpContext.Features.Get<IAuthenticateResultFeature>()? .AuthenticateResult?.Properties?.GetTokenValue("access_token" )?.ToString() ?? string .Empty; if (!StringValues.IsNullOrEmpty(accessToken)) { return RateLimitPartition.GetTokenBucketLimiter(accessToken, _ => new TokenBucketRateLimiterOptions { TokenLimit = myOptions.TokenLimit2, QueueProcessingOrder = QueueProcessingOrder.OldestFirst, QueueLimit = myOptions.QueueLimit, ReplenishmentPeriod = TimeSpan.FromSeconds(myOptions.ReplenishmentPeriod), TokensPerPeriod = myOptions.TokensPerPeriod, AutoReplenishment = myOptions.AutoReplenishment }); } return RateLimitPartition.GetTokenBucketLimiter("Anon" , _ => new TokenBucketRateLimiterOptions { TokenLimit = myOptions.TokenLimit, QueueProcessingOrder = QueueProcessingOrder.OldestFirst, QueueLimit = myOptions.QueueLimit, ReplenishmentPeriod = TimeSpan.FromSeconds(myOptions.ReplenishmentPeriod), TokensPerPeriod = myOptions.TokensPerPeriod, AutoReplenishment = true }); }); }); var app = builder.Build();app.UseAuthorization(); app.UseRateLimiter(); app.MapGet("/" , () => "Hello, World!" ); app.MapGet("/jwt" , (HttpContext context) => $"Hello {GetUserEndPointMethod(context)} " ) .RequireRateLimiting(jwtPolicyName) .RequireAuthorization(); app.MapPost("/post" , (HttpContext context) => $"Hello {GetUserEndPointMethod(context)} " ) .RequireRateLimiting(jwtPolicyName) .RequireAuthorization(); app.Run(); static string GetUserEndPointMethod (HttpContext context ) $"Hello {context.User.Identity?.Name ?? "Anonymous" } " + $"Endpoint:{context.Request.Path} Method: {context.Request.Method} " ;
具有 ConcurrencyLimiter、 TokenBucketRateLimiter和 授权的限制器 以下示例:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 var getPolicyName = "get" ;var postPolicyName = "post" ;var myOptions = new MyRateLimitOptions();builder.Configuration.GetSection(MyRateLimitOptions.MyRateLimit).Bind(myOptions); builder.Services.AddRateLimiter(_ => _ .AddConcurrencyLimiter(policyName: getPolicyName, options => { options.PermitLimit = myOptions.PermitLimit; options.QueueProcessingOrder = QueueProcessingOrder.OldestFirst; options.QueueLimit = myOptions.QueueLimit; }) .AddPolicy(policyName: postPolicyName, partitioner: httpContext => { string userName = httpContext.User.Identity?.Name ?? string .Empty; if (!StringValues.IsNullOrEmpty(userName)) { return RateLimitPartition.GetTokenBucketLimiter(userName, _ => new TokenBucketRateLimiterOptions { TokenLimit = myOptions.TokenLimit2, QueueProcessingOrder = QueueProcessingOrder.OldestFirst, QueueLimit = myOptions.QueueLimit, ReplenishmentPeriod = TimeSpan.FromSeconds(myOptions.ReplenishmentPeriod), TokensPerPeriod = myOptions.TokensPerPeriod, AutoReplenishment = myOptions.AutoReplenishment }); } return RateLimitPartition.GetTokenBucketLimiter("Anon" , _ => new TokenBucketRateLimiterOptions { TokenLimit = myOptions.TokenLimit, QueueProcessingOrder = QueueProcessingOrder.OldestFirst, QueueLimit = myOptions.QueueLimit, ReplenishmentPeriod = TimeSpan.FromSeconds(myOptions.ReplenishmentPeriod), TokensPerPeriod = myOptions.TokensPerPeriod, AutoReplenishment = true }); }));
有关完整Program.cs文件,请参阅示例存储库 。
使用速率限制测试终结点 在将使用速率限制的应用部署到生产环境之前,请对应用进行压力测试,以验证所使用的速率限制器和选项。 例如,使用 BlazeMeter 或 Apache JMeter HTTP (S 等工具创建 JMeter 脚本) 测试脚本记录器 ,并将该脚本加载到 Azure 负载测试 。
使用用户输入创建分区会使应用容易受到 拒绝服务 (DoS) 攻击。 例如,在客户端 IP 地址上创建分区会使应用容易受到采用 IP 源地址欺骗的拒绝服务攻击。 有关详细信息,请参阅 BCP 38 RFC 2827 网络入口筛选:击败采用 IP 源地址欺骗的拒绝服务攻击 。
其他资源
来源信息
原文 :ASP.NET Core 中的速率限制中间件 Arvin Kahbazi 、 Maarten Balliauw 和 Rick Anderson